External risk isn’t just a theoretical concern—it’s a daily, evolving threat that originates beyond your organization’s perimeter. Organisations grapple with a relentless barrage of threats to their invaluable information assets. Information Security Risk Management (ISRM) is the established discipline focused on identifying, assessing, and treating these risks to protect data confidentiality, integrity, and availability.
While traditional ISRM often centers on internal defenses – securing systems and networks an organization directly controls – a significant and rapidly expanding risk vector lurks outside these perimeters. At ISRM Technologies, we assert that a modern ISRM strategy must comprehensively address this external frontier. We specialize in managing and mitigating the critical, often overlooked, risks posed by your sensitive data once it’s exposed beyond your direct control.
Redefining ISRM: From an Internal Focus to an External Lens
Historically, Cyber Security and Threat Intelligence functions within ISRM involve identifying critical internal assets (databases, servers, applications), pinpointing vulnerabilities within those systems (software flaws, configuration errors), understanding threats that could exploit them (malware, sophisticated actors, insider threats), and deploying controls (firewalls, access policies, patching) aligned with the organization’s risk tolerance. This internal focus is fundamental.
However, an organization’s digital footprint invariably extends far beyond its firewalls. This is where ISRM must evolve. We define this evolution through the lens of Exogenous Exposure Intelligence – the state of your sensitive data residing on systems and platforms outside your direct operational control. This exposure could stem from accidental leaks, third-party breaches, misconfigured cloud services or network devices, public code repositories, or illicit marketplaces on the dark web. This external presence creates a substantial blind spot if ISRM practices remain solely inward-looking.
Exogenous Exposure Intelligence (EEI): The Core of Modern ISRM
To illuminate and address this external blind spot, ISRM Technologies champions a specialized discipline integral to modern ISRM: Exogenous Exposure Intelligence (EEI). EEI is the systematic practice of discovering, analyzing, and managing the risks associated with an organization’s sensitive data exposed on external systems. It’s about proactively understanding:
- What confidential information has been compromised or leaked externally?
- Where does it reside outside your network?
- How critical is this exposure?
- What are the potential impacts and the optimal remediation pathways?
AI-Driven Exposure Detection
ISRM Technologies fuses cutting-edge AI with multi-source intelligence to expose hidden data leaks across the entire web ecosystem.
Our proprietary machine learning engines continuously crawl the surface web, deep/dark web forums, paste sites, code repositories, and peer-to-peer channels—far beyond the reach of conventional search engines (aon.com). This method of exogenous exposure detection mirrors elite intelligence methodologies. As noted by the U.S. Defense Department, ~80% of their intelligence originates from open-source data (flashpoint.io)—ISRM automates that model at web scale.
We pair advanced Natural Language Processing (NLP) and pattern recognition to filter billions of data points daily (cybelangel.com), enabling us to triage and validate risks before adversaries can act.
What We Detect
- Stolen credentials – Usernames, passwords, API keys, SSH tokens leaked or sold on underground forums and paste sites.
- Proprietary data leaks – Source code, architectural diagrams, customer databases exposed via missteps or insiders.
- Misconfigured assets – Open cloud storage, unsecured databases, or forgotten endpoints discovered via non-public scans.
- Impersonation campaigns – Phishing sites, fake apps, and cloned social media profiles flagged before user damage.
Each threat is enriched with deep context—threat actor identity, breach timeline, related incidents—so remediation can be rapid and prioritized (aon.com, flashpoint.io).
Proprietary Intelligence & Data Assets
ISRM builds market-leading threat models from exclusive intelligence streams—not just public data.
Beyond OSINT, we maintain private sensor networks, trusted underground informants (HUMINT), and invite-only access to restricted data communities. Our custom-trained AI is fluent in multi-language chatter, using NLP to interpret slang, obfuscation, and regional dialects from hacker marketplaces.
Our Exogenous Exposure Intelligence (EEI) platform gets smarter with every takedown and near miss—continuously learning, adapting, and improving detection.
What Sets Us Apart
- Proprietary Machine Learning – Custom-built algorithms trained on known breach tactics, techniques, and procedures (TTPs).
- Natural Language Intelligence – Multilingual parsing of underground forums, chat logs, and threat documentation.
- Human Augmentation – Expert analysts and HUMINT operatives verify high-risk leaks and investigate anomalies.
- Hidden-Source Crawling – 24/7 scanning of encrypted networks, anonymous platforms, private Pastebins, and threat actor channels.
This end-to-end intelligence pipeline makes ISRM a category-defining leader. We don’t just gather raw OSINT—we transform it into actionable exposure intelligence, integrated with IT workflows and automated remediation triggers.
Once an exposure is flagged, instant alerts and automated response playbooks ensure rapid containment—a level of orchestration rare in the industry (cybelangel.com).
Our ISRM Process: The Lifecycle of External Risk Mitigation
Our approach to ISRM, powered by EEI, provides an end-to-end solution for managing exogenous exposure risks. This can be visualized as a continuous lifecycle:
1. IDENTIFY: AI & Human-Led Discovery: We employ sophisticated techniques (symbolized by radar scanning the digital globe) to continually search the vast expanse of the surface, deep, and dark web. Our mission is to find and discursively investigate specific instances where your confidential data has been exposed.
2. ANALYSE (EEI): Risk Assessment & Intelligence: Once potential data exposure is identified, our EEI process kicks in (visualize a brain processing information or an analytical report). We analyze its context, sensitivity, and potential impact. We provide detailed reporting and actionable intelligence, helping you understand your external digital footprint and empowering proactive mitigation strategies.
3. MITIGATE & REMOVE: Action & Resolution: For critical exposures, we initiate and coordinate targeted action (represented by a shield, gavel, or eraser). This can range from enabling internal mitigation based on our findings to, where appropriate and feasible, our specialist legal team coordinating data erasure campaigns. Leveraging regulations like GDPR’s ‘Right to Erasure’ and advanced data obfuscation techniques, we can compel data controllers hosting the exposed information to remove it, neutralizing the threat at its source.
ISRM (EEI Focus) vs. Traditional Cyber Threat Framework: Clarifying the Distinctions
Understanding the distinct roles of various security functions is key. ISRM, with a core focus on EEI as practiced by ISRM Technologies, occupies a unique and vital space. Consider this comparison:
| Feature/Focus | Cyber Security | Threat Intelligence | ISRM (EEI Focus – ISRM Technologies) |
| Primary Domain | Internal Network & Systems | External Threat Landscape (Adversaries, TTPs) | External Internet, Deep & Dark Web (Your Exposed Data) |
| Primary Goal | Defend perimeter & controlled assets | Inform defenses with attacker & threat context | Find, Analyze & Manage Risk from your specific exposed data |
| Core Questions | “Are our systems secure?” “Is the firewall up?” | “Who might attack us?” “What are their methods?” | “Is our sensitive data exposed externally? Where? How critical?” |
| Key Activities | Patching, Firewall Mgmt, Endpoint Security, SIEM | Tracking Threat Actors, Malware Analysis, IOC Feeds | OSINT, Dark Web Monitoring, Data Leak Analysis, Takedowns |
| Typical Outputs | Secure Configurations, Blocked Attacks, Incident Alerts | Threat Reports, IOC Lists, Attacker Profiles | Exposed Data Reports, Risk Assessments, Removal Actions |
| Analogy | Castle Wall Guards & Internal Patrols | Scouts Reporting Enemy Movements & Tactics | External Recon & Cleanup Crew retrieving your lost secrets |
Visualizing External Risk: An ISRM Technologies Equation
While precise risk quantification is multifaceted, the external risk that ISRM Technologies addresses can be conceptualized as follows:
External Risk = (Sensitivity of Exposed Data x Ease of Discovery/Exploitation x Potential Impact) – Proactive External Mitigation (EEI)
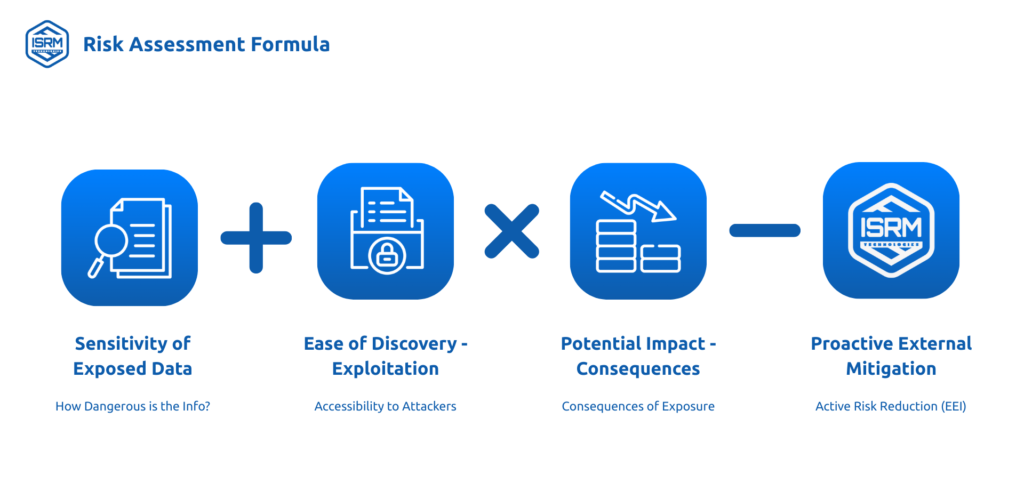
- Sensitivity of Exposed Data: How critical is the information? (e.g., Administrator credentials pose a far greater immediate risk than a public-facing marketing brochure).
- Ease of Discovery/Exploitation: How readily available is the data? (e.g., Data on the surface web via a search engine vs. data on an obscure dark web market requiring specialized access).
- Potential Impact: What are the consequences if this data is misused? (e.g., Financial loss, reputational damage, IP theft, legal penalties, operational disruption – aligning with observed impacts like those reported by IBM on data breach costs).
- Proactive External Mitigation (EEI): This is the critical reductive factor ISRM Technologies introduces. By actively finding exposed data (Identification), assessing its risk (EEI), and initiating mitigation or removal (Action), we directly reduce the overall external risk equation for our clients.
Why ISRM, through EEI, is a Distinct & Crucial Discipline
ISRM, particularly when augmented by the EEI discipline pioneered by ISRM Technologies, is not merely an extension of existing cybersecurity functions or a sub-discipline of general threat intelligence. It stands as an essential field in its own right due to:
Unique Focus: While cyber security focuses inward and traditional threat intelligence monitors general external threats (actors, malware), EEI specifically addresses your organization’s sensitive data already residing outside your direct control.
Specialized Skill Set: Effective EEI demands deep expertise in OSINT, dark web investigation, data correlation, AI-driven analysis of unstructured and often obfuscated data, and navigating complex legal and technical takedown procedures – capabilities distinct from typical Security Operations Center (SOC) or general threat analysis roles.
Addressing a Critical Gap: EEI closes a vital vulnerability exposed when organizations focus predominantly on perimeter defense or generalized threat actor TTPs. It directly addresses the risk emanating from information assets that have already been compromised or inadvertently exposed.
Navigating the Rising Tide of Exposures
In the contemporary digital ecosystem, data exposure is not a matter of if, but when, where, and how critically. As organizations generate, process, and share more data than ever, their external attack surface continuously expands. The repercussions are severe: IBM’s 2024 report indicated data breaches cost companies an average of $4.88 million per incident (risen from $4.45M in 2023), creating pathways for devastating financial losses, reputational ruin, intellectual property theft, legal entanglements, and operational chaos.
Traditional security measures, while indispensable, are insufficient to counter this escalating challenge in isolation. Proactive management of your external data footprint, as an integral component of your Information Security Risk Management strategy, is no longer optional—it is essential. This is where ISRM, viewed through the specialist lens of Exogenous Exposure Intelligence (EEI), becomes indispensable.
ISRM Technologies integrates specialized threat research with advanced EEI (Exogenous Exposure Intelligence) to systematically detect, assess, and mitigate risks from externally exposed data. Our platform delivers actionable intelligence at scale—enabling teams to close critical visibility gaps, prioritize high-risk exposures, and strengthen their overall security posture.
Sources:
- Aon Cyber Risk Report – www.aon.com
- Flashpoint: Open Source Intelligence Insights – www.flashpoint.io
- IBM Cost of a Data Breach Report – www.ibm.com
- CybelAngel: Digital Risk Protection Solutions – www.cybelangel.com
- MITRE ATT&CK Framework – attack.mitre.org
- U.S. Department of Defense OSINT Practices – Public domain publications
- Rapid7 – rapid7.com




